Bill Nelson

Life in the Impact Zone: Surfin’ the Turbulent Waters
In surfing, there’s a place known as the impact zone—that stretch of water just beyond the calm, where the waves crash with force and fury. It’s where the action happens, the..
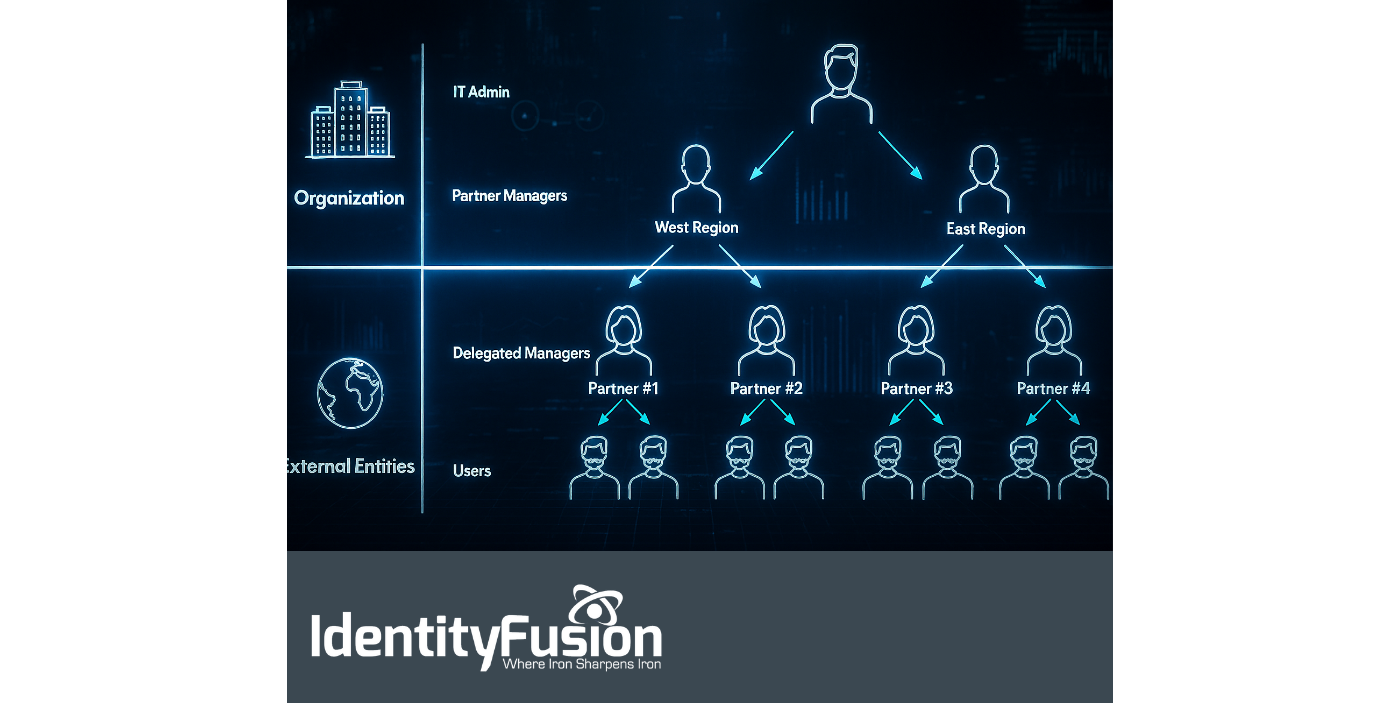
The Hidden Risk in Your Partner Network: Why B2B IAM Can’t Be Ignored
One of the most consistently challenging aspects of our work as a consulting agency is the onboarding process with new clients. It’s rarely the paperwork or compliance training..

Measure Twice, Cut Once
When I bought my first house some 30 years ago, I was young, ambitious, and wildly confident in my ability to take on home improvement projects I had no business tackling. It was..

The Strategic Value of Failing Early
Let’s be honest—technology is hard. Even the most seasoned teams, armed with detailed roadmaps, meticulous designs, and experienced architects, will eventually face the same..
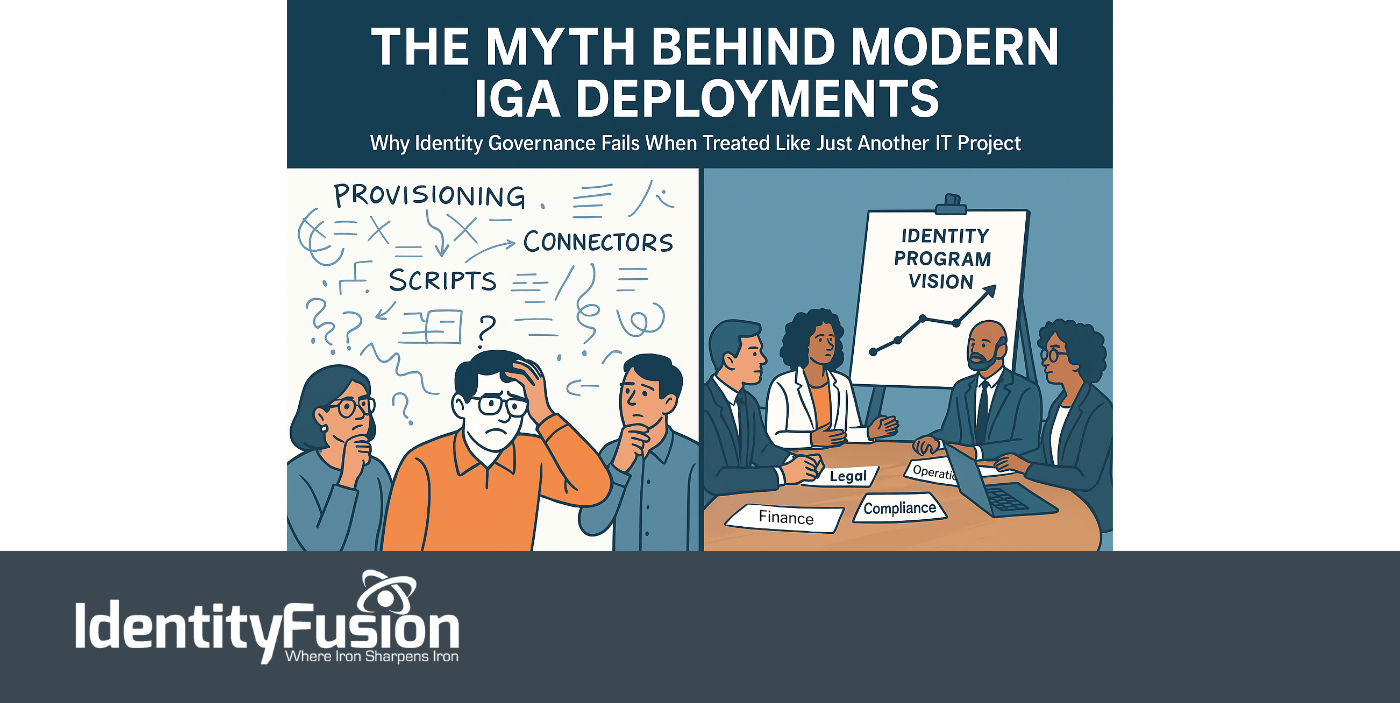
The Myth Behind Modern IGA Deployments
Identity is no longer just a security layer—it’s now central to everything an organization does. From onboarding employees and enabling partner collaboration to powering seamless..
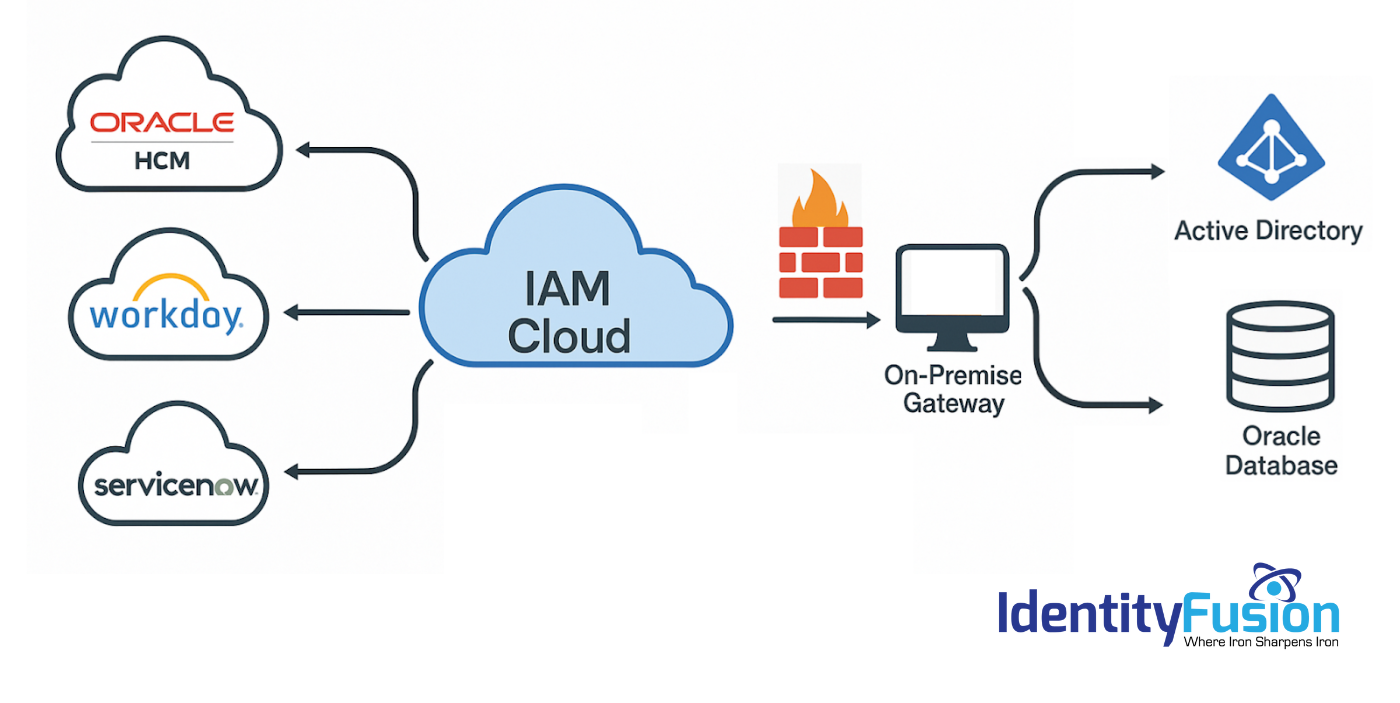
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..
.png)
Identity Fusion Announces Strategic Partnership with Dock Labs to Bridge the Gap Between Legacy IAM and Next-Generation Identity Solutions
At Identity Fusion, our mission has always been to help organizations navigate the ever-evolving identity and access management (IAM) landscape with confidence and clarity. As..

Future-Proofing Identity: Bridging the Gap to Identity 3.0
Identity security is more critical now than it has ever been. Organizations have invested heavily in legacy identity implementations, including enterprise directory services,..

The State of Identity 3.0: Where Are We Now?
The evolution of digital identity is well underway, with Identity 3.0 bringing a decentralized, user-centric approach that could revolutionize how we verify ourselves online...

New Year, New Beginnings: Embracing the Future of Identity and Access Management in 2025
As the calendar turns to 2025, organizations are facing a rapidly evolving digital landscape. With increasing cyber threats, expanding digital ecosystems, and rising consumer..

Identity 2.0 vs Identity 3.0: A Comparative Analysis
As digital identity evolves, the limitations of traditional systems, often referred to as Identity 2.0, are becoming increasingly apparent. The rise of Identity 3.0 brings a..

The Road to Identity 3.0: Challenges Associated with Implementing a New Identity Paradigm
Imagine a world where you never have to worry about your identity being stolen, where proving who you are is as easy as a tap on your phone, and where you—not some corporation or..
