Identity Fusion Blog: Cybersecurity

2026 and Beyond: Identity at the Breaking Point
As I look toward 2026, I hear a familiar refrain growing louder across conference stages, analyst reports, blog posts, and vendor roadmaps: identity is the new perimeter. Many..

Trust Is No Longer Binary
For years, organizations treated identity like a lock on a door. Authenticate the user, check the box, all’s good, move on. That model made sense when identities were mostly..

Analysts, Oracles, and the $80,000 Bake Sale
Walking out of the identity conference in Texas feels a bit like leaving a Renaissance fair where everyone forgot their costumes but kept the ticket prices. Vendors pulled me..

Can IAM 3.0 End Brand Impersonation?
Why Continuous Authentication Must Protect Both the User and the Application

A 610 Billion Dollar Ponzi Scheme?
When I saw these headlines the first thing I did was look for a credible news source, I didn't find one. The rumor of a $610 billion AI Ponzi scheme didn’t surprise me; these..

The New Blind Spot in IAM: Why Non- Human Identities Are Quietly Undermining Your Cybersecurity Investment
In most boardrooms, when identity security is mentioned, the focus defaults to people, employees, contractors, and customers. But in today’s digital enterprise, the biggest..

Where to Begin the Zero Trust Journey: Securing IAM with Least Privileged Access
Today organizations must come to terms with a stark truth, the perimeter is gone. Old security thinking offers little to no protection in this borderless realm. If you're still..
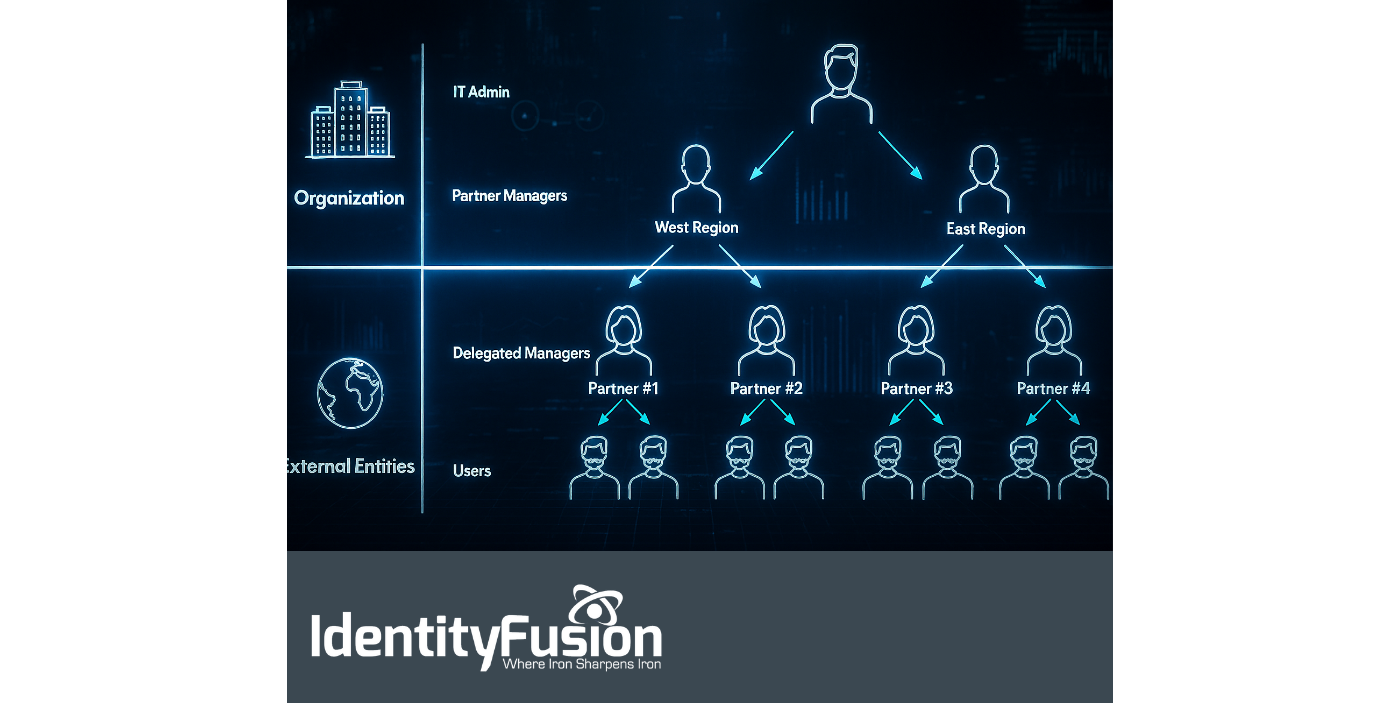
The Hidden Risk in Your Partner Network: Why B2B IAM Can’t Be Ignored
One of the most consistently challenging aspects of our work as a consulting agency is the onboarding process with new clients. It’s rarely the paperwork or compliance training..

Measure Twice, Cut Once
When I bought my first house some 30 years ago, I was young, ambitious, and wildly confident in my ability to take on home improvement projects I had no business tackling. It was..
%20Management%20.png)
The State of Non-Human Identity (NHI) Management
As digital ecosystems grow increasingly complex, so too do the identities operating within them. No longer confined to human users, identity and access management (IAM) strategies..
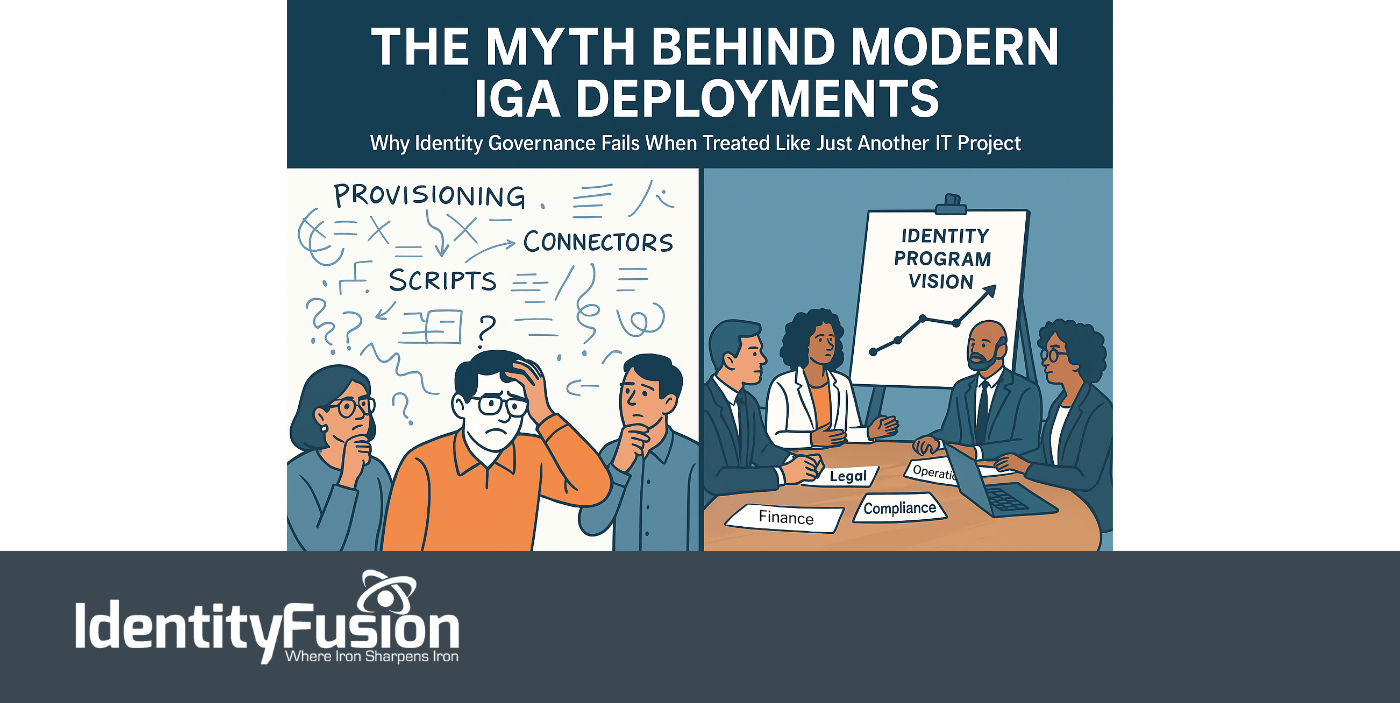
The Myth Behind Modern IGA Deployments
Identity is no longer just a security layer—it’s now central to everything an organization does. From onboarding employees and enabling partner collaboration to powering seamless..

Meet the Shakers and Movers of Identity at Identiverse — Las Vegas, Next Week
In an age when the world pivots on the axis of trust, those of us shaping the future of identity stand at a rare and vital crossroads. Next week, that crossroads has a name:..
