Identity Fusion Blog: SecureAccess

Breach Detection Takes Too Long: Why Even “New” IAM Systems Need Modernization
IBM’s research lays it bare: it takes 292 days on average to detect a compromised non-human identity (NHI). That’s nearly 10 months, an eternity in the digital battlefield. By..

The Genius Behind Security
I often write about the challenges that define cybersecurity today, the relentless push and pull between defenders and attackers, the fragile balance between Identity and Access..
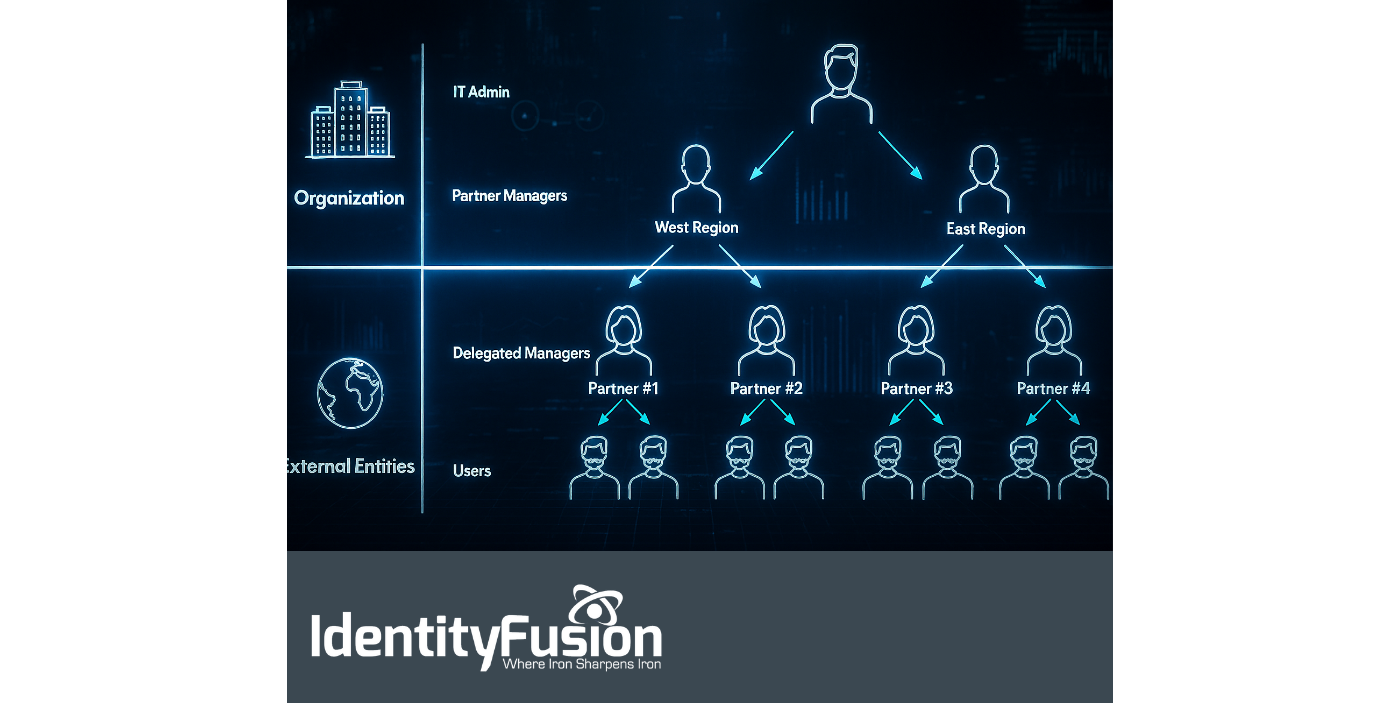
The Hidden Risk in Your Partner Network: Why B2B IAM Can’t Be Ignored
One of the most consistently challenging aspects of our work as a consulting agency is the onboarding process with new clients. It’s rarely the paperwork or compliance training..
The Myth Behind Modern IGA Deployments
Identity is no longer just a security layer—it’s now central to everything an organization does. From onboarding employees and enabling partner collaboration to powering seamless..

Database Access Control: Strategies for Protecting Sensitive Information
Database access control is a method of allowing access to a company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict..
