Identity Fusion Blog: DigitalTrust

The Gate Was Always the Defense
Why identity has always been infrastructure, and always the defense...

IAM World War 3: The Battle for Digital Trust Has Begun
Every industry reaches moments when the ground shifts so completely that the old maps become liabilities. Identity and Access Management is standing squarely in one of those..

Healthcare’s Reckoning: Why Identity Is Now a Patient Safety Issue
Healthcare has always understood risk. Long before “cyber” entered the vocabulary, clinicians learned to respect infection control, chain of custody, redundancy, and fail-safe..

2026 and Beyond: Identity at the Breaking Point
As I look toward 2026, I hear a familiar refrain growing louder across conference stages, analyst reports, blog posts, and vendor roadmaps: identity is the new perimeter. Many..

Can IAM 3.0 End Brand Impersonation?
Why Continuous Authentication Must Protect Both the User and the Application

The Invisible Perimeter
Business today doesn’t end at the corporate firewall. Financial institutions, insurers, manufacturers, and service providers now operate in a mesh of partnerships, agents,..
When “Users” Aren’t Human: APIs, Bots, and Agentic AI as First-Class Citizens
INSIGHT SERIES 4 of 4 Legacy IAM is now the weakest link in the enterprise chain. The “users” in your systems aren’t human at all, they’re APIs, bots, service accounts and the..

Fabric, Not Fortress: Building IAM for Modular Orchestration
INSIGHT SERIES 3 of 4 This article is the third chapter in our four-part series on the end of legacy IAM and the rise of IAM 3.0. The cracks in the old platform fortress are no..

The Silent Revolution
INSIGHT SERIES 2 of 4 This article is the second chapter of a four-part series. The clock is ticking on legacy IAM. The “old guard” wasn’t built for AI, bots, APIs, or non-human..
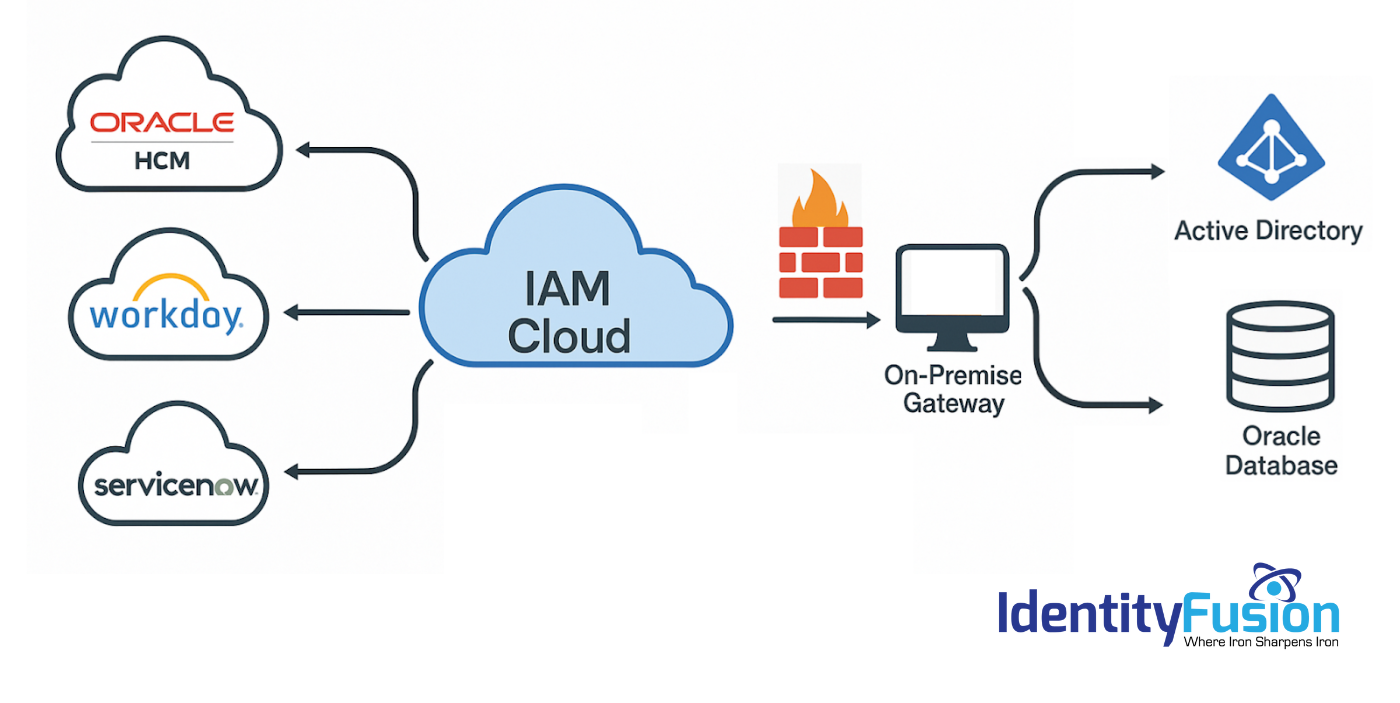
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..

The Emerging Future of Identity and Access Management: AI, Quantum Computing, and the Dawn of IAM 3.0
Part One of Two We all see that cyber threats are scaling faster than governance frameworks can adapt, the emergence of artificial intelligence (AI), machine learning (ML), and..

New Year, New Beginnings: Embracing the Future of Identity and Access Management in 2025
As the calendar turns to 2025, organizations are facing a rapidly evolving digital landscape. With increasing cyber threats, expanding digital ecosystems, and rising consumer..
