Identity Fusion Blog: CloudSecurity

The Gate Was Always the Defense
Why identity has always been infrastructure, and always the defense...

Can IAM 3.0 End Brand Impersonation?
Why Continuous Authentication Must Protect Both the User and the Application

Who Blew Up Your Attack Surface?
The modern network hums with voices you can't see. Not people, machines. Containers, APIs, CI/CD agents, cloud functions, service accounts, scheduled jobs, and AI agents: an..

Where to Begin the Zero Trust Journey: Securing IAM with Least Privileged Access
Today organizations must come to terms with a stark truth, the perimeter is gone. Old security thinking offers little to no protection in this borderless realm. If you're still..
%20Management%20.png)
The State of Non-Human Identity (NHI) Management
As digital ecosystems grow increasingly complex, so too do the identities operating within them. No longer confined to human users, identity and access management (IAM) strategies..

Non-Human Identities: The Fastest-Growing Threat in IAM and Cybersecurity
In today’s digital battlefield, not all users are flesh and blood. In fact, most aren’t. The silent majority behind modern infrastructure, the service accounts, machine..
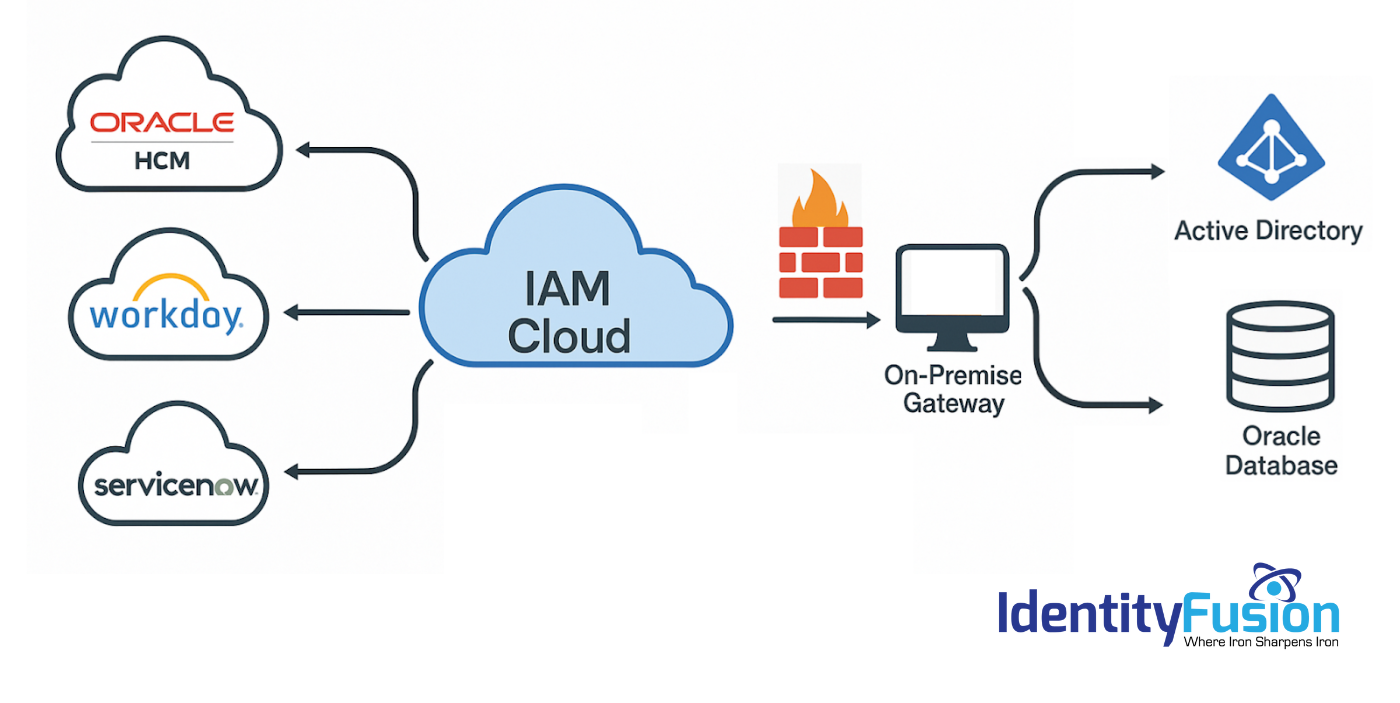
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..
.png)
Identity Fusion Announces Strategic Partnership with Dock Labs to Bridge the Gap Between Legacy IAM and Next-Generation Identity Solutions
At Identity Fusion, our mission has always been to help organizations navigate the ever-evolving identity and access management (IAM) landscape with confidence and clarity. As..
