Identity Fusion Blog: IAM (2)

The New Blind Spot in IAM: Why Non- Human Identities Are Quietly Undermining Your Cybersecurity Investment
In most boardrooms, when identity security is mentioned, the focus defaults to people, employees, contractors, and customers. But in today’s digital enterprise, the biggest..

Where to Begin the Zero Trust Journey: Securing IAM with Least Privileged Access
Today organizations must come to terms with a stark truth, the perimeter is gone. Old security thinking offers little to no protection in this borderless realm. If you're still..
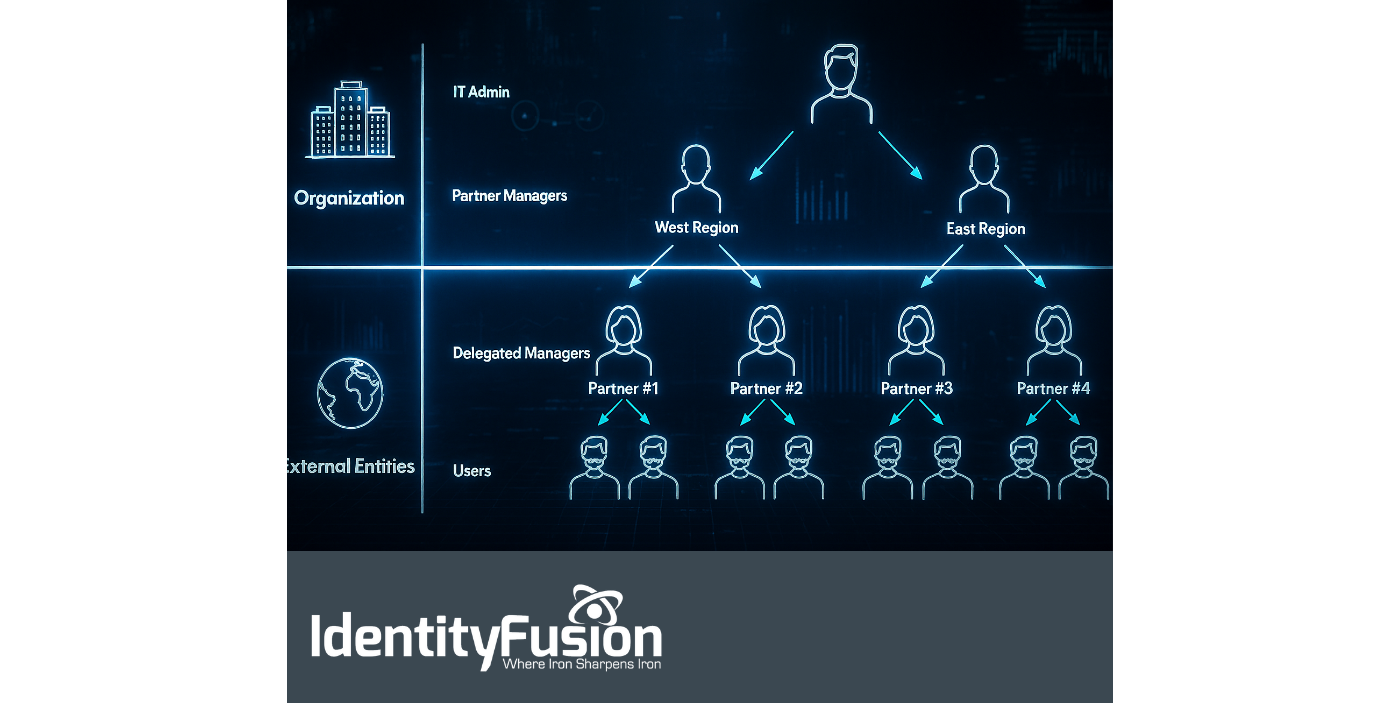
The Hidden Risk in Your Partner Network: Why B2B IAM Can’t Be Ignored
One of the most consistently challenging aspects of our work as a consulting agency is the onboarding process with new clients. It’s rarely the paperwork or compliance training..

Why You Must Start Planning for IAM 3.0 Today
There’s an old saying: “The best time to plant a tree was twenty years ago. The second best time is today.” When it comes to Identity and Access Management (IAM), we no longer..
%20Management%20.png)
The State of Non-Human Identity (NHI) Management
As digital ecosystems grow increasingly complex, so too do the identities operating within them. No longer confined to human users, identity and access management (IAM) strategies..
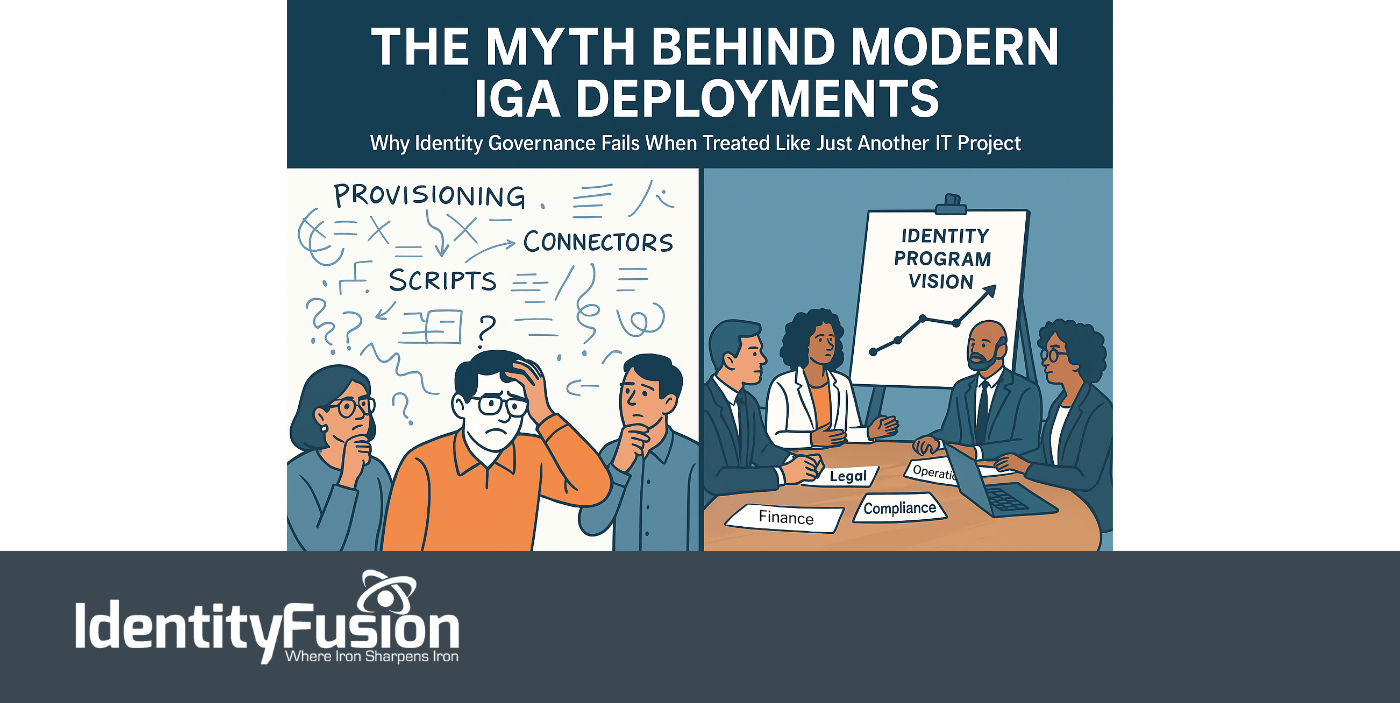
The Myth Behind Modern IGA Deployments
Identity is no longer just a security layer—it’s now central to everything an organization does. From onboarding employees and enabling partner collaboration to powering seamless..

Meet the Shakers and Movers of Identity at Identiverse — Las Vegas, Next Week
In an age when the world pivots on the axis of trust, those of us shaping the future of identity stand at a rare and vital crossroads. Next week, that crossroads has a name:..

Non-Human Identities: The Fastest-Growing Threat in IAM and Cybersecurity
In today’s digital battlefield, not all users are flesh and blood. In fact, most aren’t. The silent majority behind modern infrastructure, the service accounts, machine..
%20in%20Retail-%20Balancing%20Security%20and%20Seamless%20Experiences.png)
AI-Driven Identity and Access Management (IAM) in Retail: Balancing Security and Seamless Experiences
To today’s modern retailer, the customer journey is no longer limited to a single store visit or a static online cart. It spans apps, kiosks, mobile devices, loyalty portals, and..
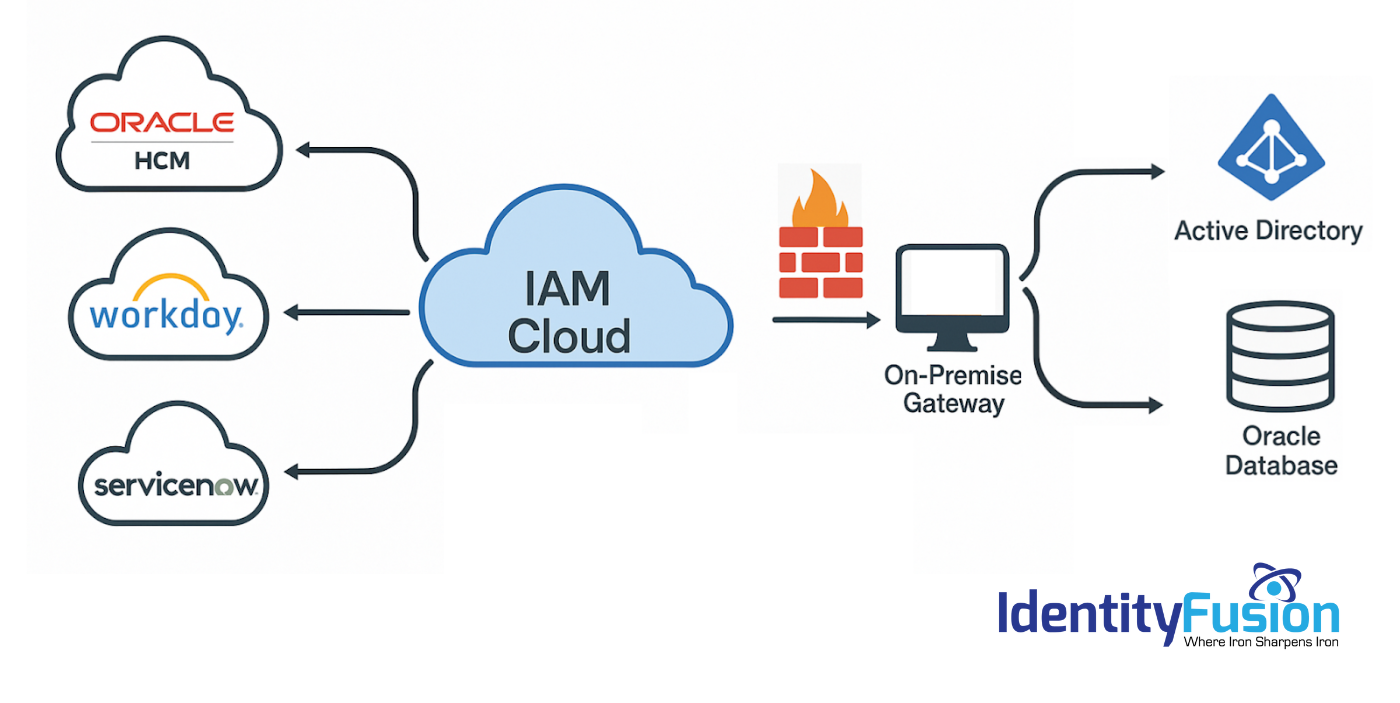
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..
Identity in the Age of AI: Why Governance Is the New Cybersecurity Imperative
In 2025, the stakes for Identity and Access Management (IAM) have never been higher. AI and machine learning are rewriting the rules of cybersecurity, and identity is at the..

