Identity Fusion Blog: DigitalTransformation

Why Visual Orchestration Is the Unsung Hero in Your IAM Modernization Journey
As Carol Kane said in Scrooged, "Sometimes you have to slap them in the face just to get their attention!" This blog is a literary slap to get your attention.
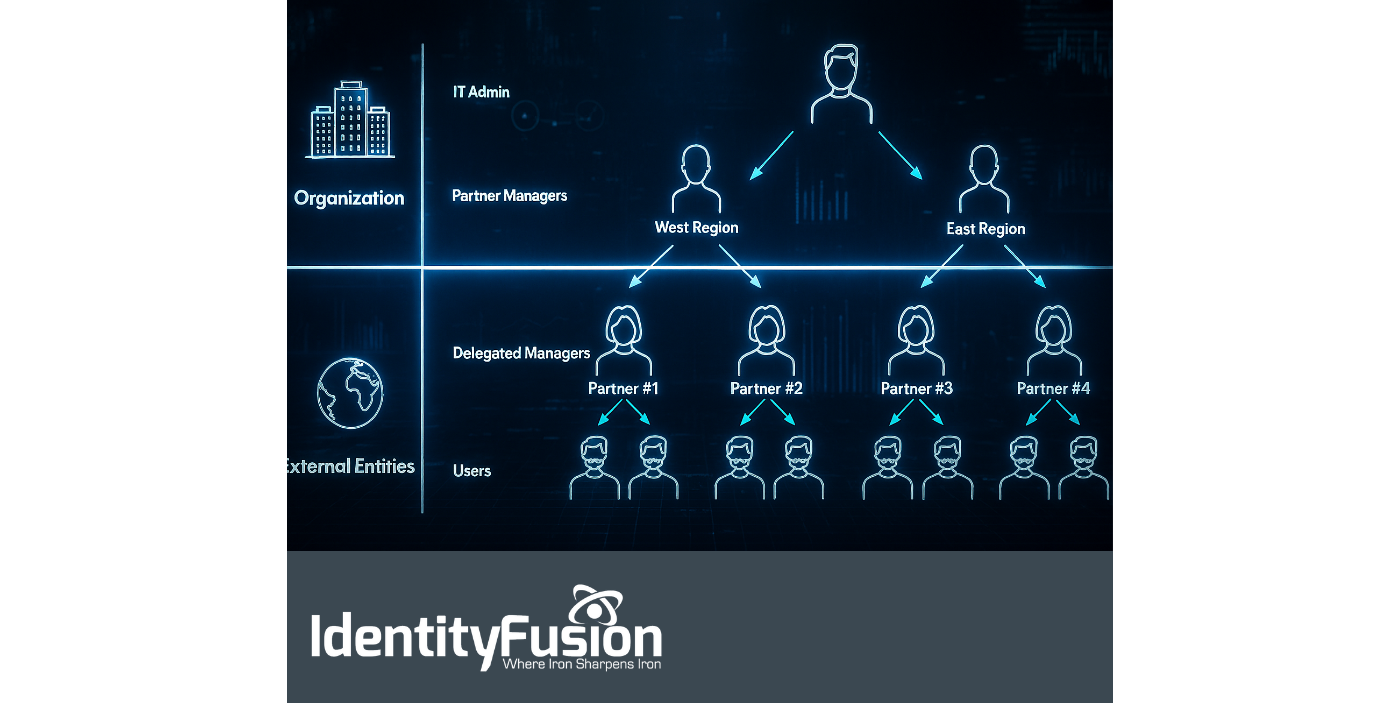
The Hidden Risk in Your Partner Network: Why B2B IAM Can’t Be Ignored
One of the most consistently challenging aspects of our work as a consulting agency is the onboarding process with new clients. It’s rarely the paperwork or compliance training..
%20Management%20.png)
The State of Non-Human Identity (NHI) Management
As digital ecosystems grow increasingly complex, so too do the identities operating within them. No longer confined to human users, identity and access management (IAM) strategies..

Non-Human Identities: The Fastest-Growing Threat in IAM and Cybersecurity
In today’s digital battlefield, not all users are flesh and blood. In fact, most aren’t. The silent majority behind modern infrastructure, the service accounts, machine..
%20in%20Retail-%20Balancing%20Security%20and%20Seamless%20Experiences.png)
AI-Driven Identity and Access Management (IAM) in Retail: Balancing Security and Seamless Experiences
To today’s modern retailer, the customer journey is no longer limited to a single store visit or a static online cart. It spans apps, kiosks, mobile devices, loyalty portals, and..

Why Typical Agile Falls Short in Large-Scale Identity, Access, and Governance Projects
It is easy to appreciate why Agile has become the default project management style for so many technology initiatives. Fast iterations, continuous feedback, and adaptable..
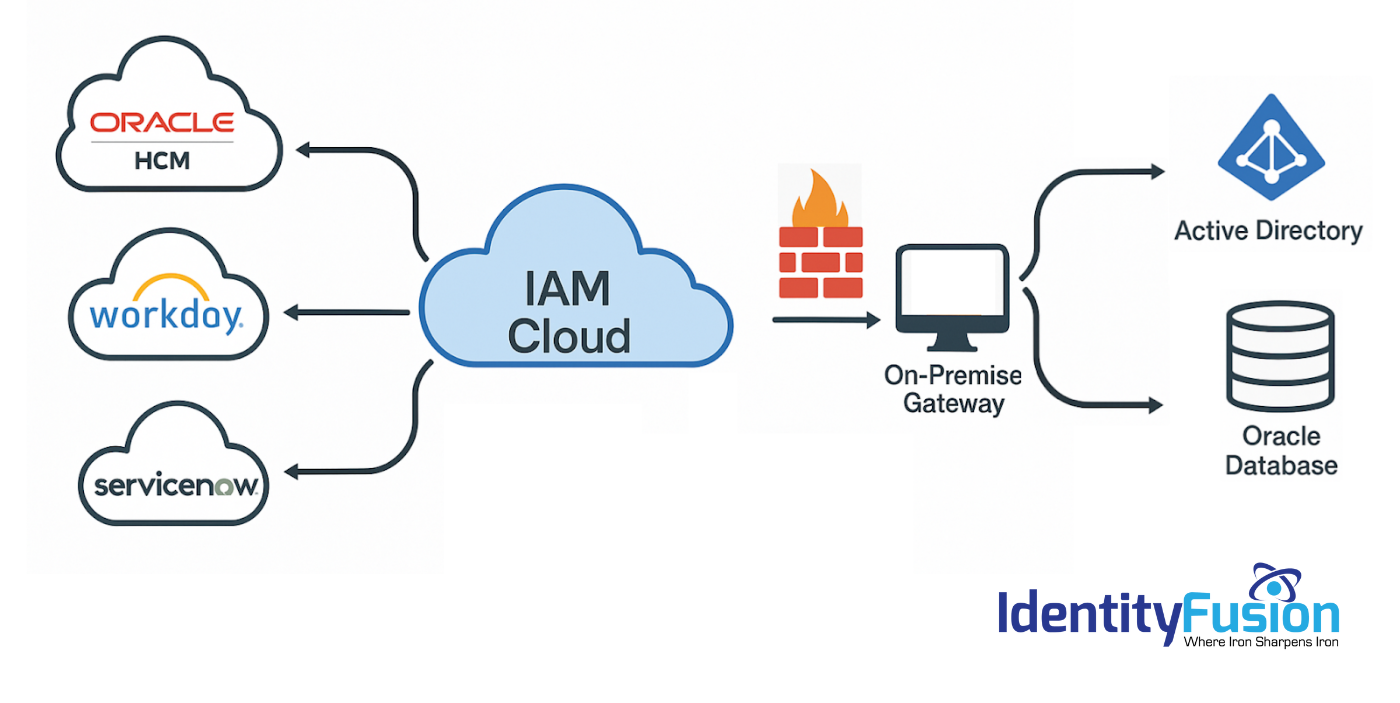
Migrating to an Identity Cloud: What the Vendors Won’t Tell You
As you explore the possibility of migrating your on-premise IAM solution to the cloud, you’ve likely heard promises of lower costs, simplified deployment, improved security, and..
.png)
Identity Fusion Announces Strategic Partnership with Dock Labs to Bridge the Gap Between Legacy IAM and Next-Generation Identity Solutions
At Identity Fusion, our mission has always been to help organizations navigate the ever-evolving identity and access management (IAM) landscape with confidence and clarity. As..

Future-Proofing Identity: Bridging the Gap to Identity 3.0
Identity security is more critical now than it has ever been. Organizations have invested heavily in legacy identity implementations, including enterprise directory services,..

The State of Identity 3.0: Where Are We Now?
The evolution of digital identity is well underway, with Identity 3.0 bringing a decentralized, user-centric approach that could revolutionize how we verify ourselves online...

New Year, New Beginnings: Embracing the Future of Identity and Access Management in 2025
As the calendar turns to 2025, organizations are facing a rapidly evolving digital landscape. With increasing cyber threats, expanding digital ecosystems, and rising consumer..

Identity 2.0 vs Identity 3.0: A Comparative Analysis
As digital identity evolves, the limitations of traditional systems, often referred to as Identity 2.0, are becoming increasingly apparent. The rise of Identity 3.0 brings a..
