How do you Implement IAM? One Bite at a Time
Contents
Introduction
Oftentimes, tasks can seem daunting when you focus on the big picture and IAM implementations are no different. Successful IAM projects take a gradual, methodical approach to the implementation and are broken down into five main phases: Analysis, Architecture, Implementation, Testing, and transition to Support.
"There is only one way to eat an elephant: a bite at a time."
- Desmond Tutu
A phased approach to identity management projects allows a company to separate implementations into manageable pieces. In each phase, the scope, costs, schedule, and deliverables are clearly defined and all parties are in agreement before continuing on to the next phase.
A common example of a phased approach to full-stack identity management projects includes deployment of a directory services layer, followed by an access management layer, and a subsequent identity provisioning layer.
Implementation of a phased approach to an identity and access management solution allows organizations to recognize an immediate return on their investment while maintaining the flexibility to alter course if necessary.
Most identity and access management solutions follow a common five-stage approach (Analyze, Architect, Implement, Test, and Support) and can be seen in the following diagram.
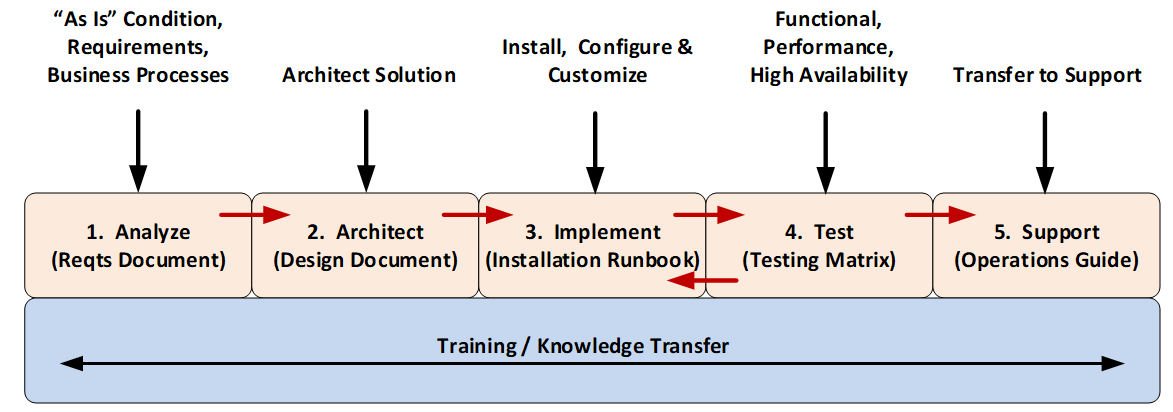
The following sections provide additional detail pertaining to each of these five stages.
Analysis and Discovery
The Analysis and Discovery stage allows you to define and share the scope among project team members. During this stage you will get a better idea of how to separate the project into multiple bite-size chunks and then determine how much — and how long — each chunk will take. This allows you to effectively budget both time and money for the project(s).
During the Analysis and Discovery stage, you will meet with both business and technical stakeholders to determine the existing (“as is”) conditions, understand business and technical drivers, and determine the processes and procedures that may direct your solution one way or another.
At the end of this stage, you should be able to clearly articulate both the existing and the future environments and understand the reasons behind why the project is being implemented.
Architecting the Solution
The goal of the Architecture stage is to take the information from the previous stage and create a design that meets the goals of the product within the constraints of the organization. Additionally, the roadmap or steps necessary to move from the current to the end state may be discussed or agreed upon. This may include deciding upon the hardware, software, data requirements, or process changes necessary to reach the end state.
At the end of this stage, you should have a clear vision of how the end state will look. This includes hardware requirements, data center buildouts, instance distributions, applications, processes, administration, and privacy and security considerations.
Once you understand what the final state will look like, you have a better idea of what it will take to move from the current state. This allows you to define the project plan and begin communicating timelines to business stakeholders.
Implementation
The Implementation stage includes all the tasks necessary to develop the end state. This includes data center build outs, operating system configuration, software installation, configuration, customization, data loading, building of administrative interfaces, and just about any other tasks necessary to reach the final state.
During this stage you will execute initial functional and user acceptance testing to ensure that you are producing a product that meets both the requirements and the needs of your end users. You will also begin producing documentation that will be used long after the project has been completed.
This includes operations and support runbooks, installation guides, and any other documentation that assists in monitoring and maintaining the products associated with the identity management solution.
It is during this stage that initial training of support personnel begins and the product is integrated with monitoring and support solutions.
The Implementation and Testing stages are tightly coupled as you may find that defects found during Testing cause the Implementation to be updated. You should plan on several iterations between these two stages before moving on to placing the solution into production.
Test
The Testing stage is necessary to determine if the final product meets the requirements established during the Analysis stage. This includes functional requirements (based on defined use cases), performance requirements (based on the needs of users or other applications), and high availability requirements (to ensure business continuity should a component fail during operation).
Once the implementation has been found to meet each of the defined requirements (of which ‘purpose of use’ is one of the most important) then it is time to transition the implementation over to the support team. The official handoff to support should include any Operations and Troubleshooting guides and details for opening support tickets with any vendors associated with the solution.
Support
The Implementation stage has been completed and the product now reflects the projected end state. The solution has been tested to ensure that it meets business, technical, and end-user requirements and the solution is now ready to transition where it can be monitored and managed by the organization’s own Support team (or a third-party Support organization).
There are times when the project development or implementation team may need to get involved in more complex troubleshooting issues, but for the most part, the Support team should be able to handle the majority of issues that might arise. This means that the Support team has been adequately trained and has the necessary prerequisite knowledge of the operating system, networks, and processes implemented in the overall solution.
Once the implementation has been transitioned to the Support team, it is now possible to begin work on the next Phase of the project where the process may start all over again at the Analysis stage.
Conclusion
Successful IAM implementation rests on a carefully structured and phased approach, requiring meticulous attention to Analysis and Discovery, Solution Architecture, Implementation, Testing, and ultimately Support. These clearly defined stages ensure smooth transitions, timeliness, cost management, and tangible deliverables, offering immediate returns and flexibility for course corrections.
Identity Fusion partners with leading healthcare providers across the United States, offering invaluable expertise in steering them through the complexities and subtleties of establishing a resilient IAM framework. This empowers them to fortify their security posture and enhance operational efficiency. Reach out to us today to elevate your organization's performance.
